Without a sound knowledge of compliance requirements, most CISOs tend to implement fractured or ad-hoc solutions which only touch a portion of the organization’s data or only certain segments of the business. Ambiguous ownership of these efforts tends to foster poor vision, undefined goals, and inaccurate measurements, which ostensibly leads to poor quality business decisions.
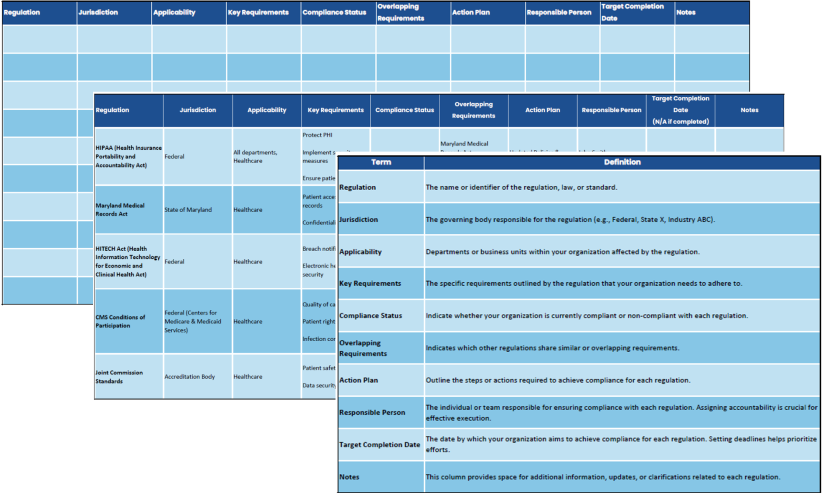
In developing a broad strategy for data privacy and compliance, organizations gravitate toward two primary methods: leveraging a compliance framework such as NIST or CIS to provide discrete, actionable steps towards maturity, or they seek out a solution provider offering some kind of compliance widget or service.
In the first scenario, compliance frameworks provide a good foundation for meeting their described outcomes but recall that most organizations are subject to dozens of regulations. Obtaining all the requisite frameworks and condensing them into a single, monolithic guidebook is rarely feasible, and seldom effective. Trying to keep this compliance casserole updated becomes a full-time job for entire departments depending on the organization’s industry, markets, and complexity.
It’s also worth noting here that an organization can be fully compliant and still suffer data loss and the subsequent aftermath. While complying with a specific regulation’s parameters may help to lessen the legal or financial impact, it does little to soften the blow to the organization’s reputation and loss of customer trust. Posting the company’s internal pricing models on social media may not violate a regulation, but it clearly isn’t a good business move.
Regarding the second option, vendor solutions are appealing for a number of reasons. Leaning on the expertise of a partner fosters an element of shared risk, and some vendors outright guarantee their services. Further, the vendor’s own mastery of the subject matter means that data privacy leaders do not need to “staff up” to meet the challenges of an evolving compliance landscape.
However, it’s also worth noting that results are only as good as the configuration of the technology and the SLAs of the provider. Nearly every data loss prevention technology comes with pre-canned templates designed to meet basic requirements of regulations such as HIPAA or PCI, but templates are designed as a one-size-fits-all solution. They are not tailor-made to the specific risk-reduction goals of the organization. To compensate, vendors will often supplement their solutions with a configuration service, but their expertise is still focused on technology and not the client organization. The vendor may have a solid grasp of GDPR, for example, but remains comparatively immature when it comes to understanding how the organization transacts business.
That’s not to say that vendor results are bad. They offer a solid starting point and are certainly better than having nothing in place at all. But CISOs who adopt a “set-it and forget-it” mindset are quickly inundated with false positives, and worse, they have little assurance about unidentified incidents where critical data has flown out the door due to sub-par configuration or a lack of training. If data stakeholders are serious about protecting their sensitive information, they must look beyond merely checking boxes off a compliance framework or acquiring more technology.
Fixing these complex issues requires a comprehensive strategy that can address everything from data usage and data classification all the way through the continued maintenance and tuning of technical controls, such as DLP or encryption. CISOs must shift their mindset from managing software suites to building, maintaining, and maturing a comprehensive Data Risk Management (DRM) Program.